MSPs Are Leveling Up
I have been feeling a monumental shift in the community over the past few years when it comes to cybersecurity. MSPs talking about cybersecurity is nothing new, however I have observed these conversations reaching a whole new level of sophistication as of late. In my opinion, this is a signal of change and one that we should start to talk about more openly.
While this new level of sophistication is no doubt creating a lot of value for the industry, it appears to also be driving a wedge straight through the middle of the MSP business model as we know it. For this reason, I wanted to get a temperature check among our community to find out where they stand on this matter and how they expect this to play out in the future.
The Big Question
To accomplish this, I decided to put a poll out to our community. I thought it would be best to boil this down into the most fundamental idea possible, to make sure that everyone in the industry could form an opinion on it. It should be a simple question that requires a relatively complex answer. Where I landed was this:
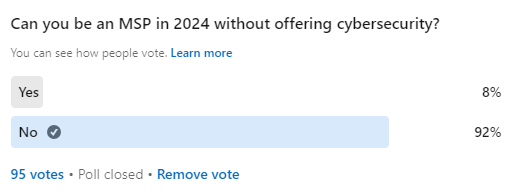
For the sake of clarity, the term “offering cybersecurity” refers to the fact that you are billing the client directly for a service that’s sole purpose is to “secure” something or someone. I would exclude any product or service that’s purpose is something else, but has security features.
To no one’s surprise, the community has taken a strong stance on this with 92% of participants answering “No.” While this is a clear signal that cybersecurity is unavoidable for MSPs in the future, there appears to be a lot of nuance in the details. That nuance was shown mostly via the anecdotal response, which I tried to capture as best as possible in this article.
An MSP Identity Crisis
If we learned one thing for certain it is that the majority of MSPs are going through a bit of an identity crisis right now, with cybersecurity being the number one contributor. They are looking inward to try to figure out where they fall on the MSP / MSSP spectrum. And yes, I use that term “spectrum” somewhat literally, because I am a firm believer that there is no hard line between them. There are plenty of MSPs that could easily pass as MSSPs but simply choose not to market themselves this way.
While there is a lot of gravitational pull toward security both from the customer side and the vendor side, I don’t believe that this is an all or nothing situation. Peter Machell of Health IT put it best when he said, “You can’t be a good MSP without considering the security of all your offerings. Should every MSP turn into an MSSP and think they can double their customer’s spend on IT by focusing on security? Hell no. Do you want to put the world out of business?”
If I understand his point correctly, it is that while every small business needs to be thoughtful about technology, they don’t need a full-on MSSP to accomplish this. This means that the blend between MSP and MSSP will continue to exist as long as the end customer’s needs support it. This need for diversity in offerings should be looked at as a feature, not a bug, and I think we need to remember that when we have these conversations.
The Ultimate Guide To Cash Flow For Managed Services
Sponsored by Alternative Payments & Zest
The Risk In Assumptions
If the customer always knew exactly where on this spectrum they were purchasing IT services, then this wouldn’t be a controversial issue at all. The problem is that they don’t and most MSPs do a poor job at communicating these details. This creates a lot of risk for the end client as the chasm between expectations and reality grows at every turn.
One of the best educators to speak on this issue is Wes Spencer, who is currently the Founder of Empath and VP of Cyber Strategy at CyberFox. His take on this issue is that “as the IT provider, the client assumes you are already handling all things cybersecurity. If you don’t communicate that clearly and have an MSA protecting yourself, you’re already on a road to trouble ahead. So you have to do something when it comes to cybersecurity.”
He’s right. Unfortunately, opting out completely isn’t a viable option because there is already a baked in assumption of responsibility. As an MSP, you can’t lead your clients to take a risk that they don’t know they are taking and that is the bottom line.
Skewed Sales & Marketing
To recall our definition of what it means to “offer cybersecurity,” any MSP that offers endpoint detection & response, cyber awareness training, or email security add-ons, technically fits the bill. While it is great that these basic needs are being met nearly industry-wide, they are just that; “basic needs.” This where a lot of the confusion comes from that is often fuelled by sales and marketing tactics that are not equally weighted in reality.
Let’s be honest, talking about how well you met your Help Desk’s SLA or your latest net promoter score doesn’t move the needle the same way the latest hack or breach does. As with all social media call and response, this leads us to continually optimize in the direction where there is the most engagement. For MSPs, this is almost always in favor of cyber-speak.
MSPs and IT Industry leaders have a lot to say on this, as the effects are being felt everywhere. As Anthony Reyes of Ikigai One explains, “I can’t stand when MSPs say they’re ‘cybersecurity first’ and lie to their customers about how secure and protected they are. They say that all their compliance needs are covered, and everything is great – meanwhile all they do is deploy an unmonitored $3 AV/EDR via their RMM, and that’s it.” Andrew Down of Vendasta shared a similar sentiment as he said “I cringe when I see MSP’s say they offer security, but no SOC, 24/7 support, complete stack (more than just AV/back-up, etc). Lots of talk, but it is important to have a strong strategy, offering, plan and execution.”
Minimalism vs. Malpractice
If there is a common thread that mostly everyone agrees on, it is that MSPs should know their limitations when it comes to cybersecurity and act accordingly. It’s okay to offer a minimal security offering as long as you represent it for what it is and have a plan for what to do whenever the client’s needs surpass your limitations.
Where this can become harmful, is when these limitations are not well defined and the strategy is simply to “learn on the job” (mostly after the damage is already done). While this was more acceptable to do back in the simpler days of hacking together client networks, it just doesn’t fly now. The stakes are too high and MSPs that are not taking a security-first approach to nearly everything they touch are committing borderline malpractice.
As security-focused IT Provider, Randall Bellows III of Be Co recalls “..thinking about the situations I walk into when taking over a new client: no patch management, open ports everywhere on a router, flat networks, lack of security automation. I remember talking to a C level COO of an MSP who served specifically industrial clients, but had no idea what Stuxnet or Sandworm is. Unfortunately, I feel like most MSP and IT professionals tack-on security after the product has been built, and don’t build the product with security.”
The “Adapt or Die” Dilemma
If you chart the path that we have been on up to this point, you realize that this is very much a transitory moment in time and that the curve will continue up and to the right. This means that security requirements will only get more sophisticated at an accelerated pace in the future. IT companies need to decide whether they want to board this train or not.
As Mike Castaldi of Wild Frog Consulting puts it, “I think what is considered to be an MSP’s minimum standard of care has – and will continue to evolve. And if an MSP is not offering (or better yet, insisting on) things like security awareness training, phishing simulation, etc. I’m not sure they meet what I’d consider to be a minimum standard of care in 2023.”
You would be surprised at how many MSPs there are out there that do not meet this “minimum standard of care” that Mike describes. I have found that this is even more common in situations where Managed Services is a secondary offering. For example, companies that primarily offer web hosting & design, digital marketing, managed print, and telecom have dipped their toe into these waters over the past decade. Now that this water is heating up from cyber requirements, these companies need to decide how committed they are and whether or not they are willing to adapt. Unfortunately, I suspect many will decide to hang on to the recurring revenue as long as they can until they are all but forced in (or out).
Opportunity Is Knocking
The good news is that there is a substantial amount of new revenue to be had for MSPs that successfully transition to a healthy cyber offering. As Analysts Robin Ody and Matthew Ball have discovered through their research at Canalys, “the forecast for this year is that total global cybersecurity managed services revenue will come to US $70.2bn, growing at 15.9%.” In a perfect world, this would be all the incentive that was needed for MSPs to adapt to the new norm and take on the risk required to get it done.
What I find most fascinating is that there seems to be a “late mover advantage” playing out. MSPs that are ramping up right now are building out a tech stack and business model that meets the exact security needs of the market opportunity and don’t have to pivot away from legacy contracts and the old way of doing business. They simply have a better, faster, and cheaper way to get it done and this may give them a clearer path to grow.
I believe that the shifting tide among the vendor community reflects this too. As Tree Achibeque of EyeOTmonitor puts it, “I don’t think anyone truly wants to miss out on new business and evolving tech. This is where MSPs should lean into companies that can assist them with their [cybersecurity] intentions. The ROI is there!” She represents just one of the thousands of vendors who are looking to be a cog in the machine that will turn local MSPs into fully-equipped cybersecurity leaders.
The Ultimate Guide To Cash Flow For Managed Services
Sponsored by Alternative Payments & Zest
Partnerships Are The Answer
Given the current state of the labor market and what it takes to bring cyber in-house, it should be no surprise that partnerships are the most viable path forward. As Mark Tishenko of Edge Networks states, “Building a cybersecurity practice in an MSP is difficult. Partnering with someone you trust is essential. Someone that will provide not just solutions, but also guidance and education to MSP customers. Companies won’t buy something they don’t understand.”
Mark brings up an excellent point here in the sense that partnerships bring a completely different voice to the customer relationship. Wes Spencer took a similar stance on this as he suggests “who owns cybersecurity at your MSP? Who communicates, oversees, and manages client cyber risk? The good news: it doesn’t always have to be you.
Depending on your revenue level and operational maturity, there’s nothing wrong with outsourcing the majority of your cybersecurity service delivery to someone else. Or perhaps you are ready to bring it in house and co-manage alongside an MDR provider. There’s multiple ways to skin this cat. But it does require some thinking and realistic expectations before you dive in head first.”
Drawing Lines In The Sand
Now that we know that partnerships are the clear solution to tackling this opportunity, it is just a matter of figuring out where to draw the lines in the sand and how to manage the client relationship in the process. The software tools are often the easy part, since MSPs resell services such as these all the time. The consulting and labor intensive part is where it gets complicated, primarily due to conflicts that may arise as a result of these new voices at the table.
To help formulate a best practice in this area, I look to Jesse Miller, who spends most of his days helping MSPs build out a cybersecurity program via his PowerPSA consultancy. As he explains, “There are two areas that I recommend focusing on when outsourcing/partnering: stuff that’s outside your skill set, and stuff that’s really repetitive and ‘below’ your skill set that takes cycles away from time better spent doing the more nuanced things for your clients. This means both on low skill and high skill ends of the spectrum relative to your cybersecurity service offering.
One thing I am probably diametrically opposed to is outsourcing vCISO. I firmly believe that’s something the MSP should NEVER outsource. You’re basically putting your client relationship in someone else’s hands – someone who’s not as deep in your client’s environment as you are. Whether it’s making recommendations counter to your standard blueprint, or just not providing a seamless experience, they will eventually ‘screw the pooch’ – and this all being visible to your VIP stakeholders. You are playing with fire if you give away this level of control to a partner.“
Conclusion
While our initial poll was somewhat lopsided, I feel like I came away from this project learning everything I needed to know about where our community stands on cybersecurity. Put simply, offering cyber is no longer optional and requires collaboration among MSPs, MSSPs, Consultants, Vendors, and Tools to accomplish. You can’t do it alone and thus attempting to do so is where most go wrong.
This also starts with the MSP. Since you own the client relationship, it is up to you to bring these resources together to suit the needs of your customer. If done correctly, it should be a great additional revenue stream, but even if the profit isn’t there, that is not an excuse to leave your client out to dry. It’s your job to create a mix of partnerships that both satisfies the client’s security requirements and generates a sustainable profit for your business. If you can’t find a way to do both, then it is possible that you shouldn’t be the one owning that client relationship after all.

SPONSORED BY ZEST